SHA-1 Generator: The Essential 2025 Guide to Hashing
Created on 18 March, 2025 • Generator Tools • 330 views • 3 minutes read
In the fast-paced digital era, securing and verifying data is a top priority for businesses, developers, and everyday users.
In the fast-paced digital era, securing and verifying data is a top priority for businesses, developers, and everyday users. If you’re on the hunt for a reliable hashing tool, the SHA-1 generator might just catch your eye. Known for its speed and historical significance, SHA-1 remains a key player in specific use cases. This SEO-optimized article will explore why a SHA-1 generator matters in 2025, how it works, and how you can use it effectively. Ready to master SHA-1 hashing? Let’s get started!
What Is a SHA-1 Generator? Unpacking the Basics
A SHA-1 generator is a tool powered by the SHA-1 (Secure Hash Algorithm 1) function, developed by the NSA in 1993. It takes any input—text, files, or binary data—and produces a 160-bit (20-byte) hash, typically shown as a 40-character hexadecimal string. Once a cornerstone of digital security, SHA-1 is still widely recognized for its role in legacy systems and non-critical applications.
Why bother with SHA-1 in 2025? While it’s no longer the gold standard for security, its efficiency and familiarity make it a practical choice for checksums, version control, and retro projects. Let’s dive deeper.
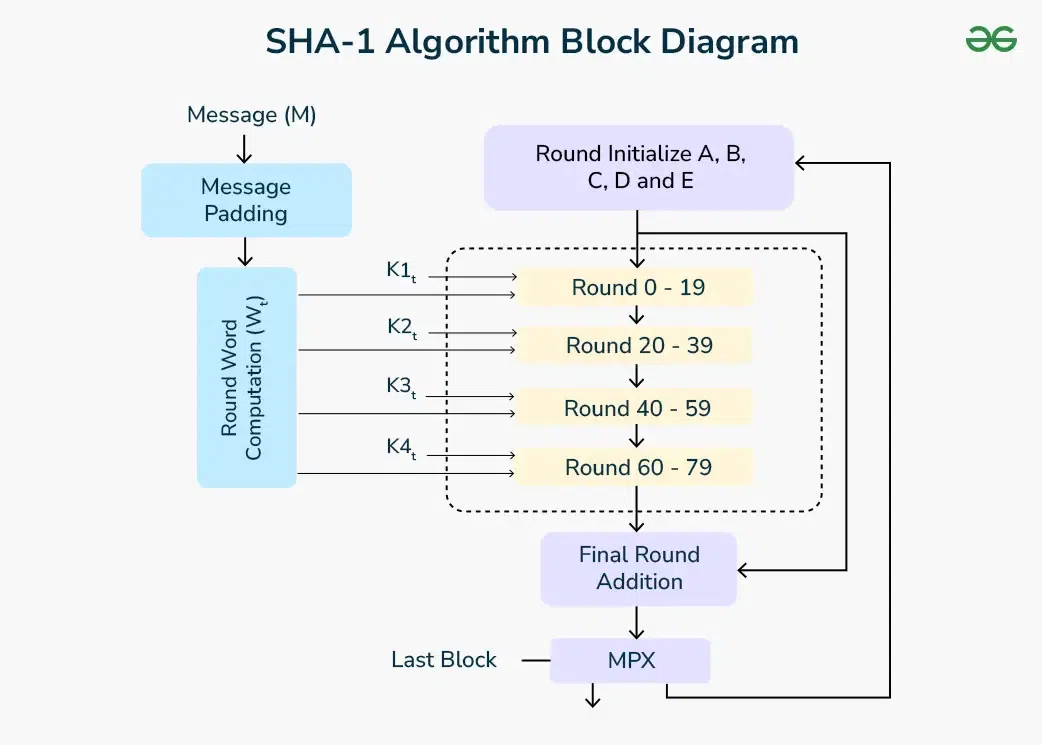
How Does a SHA-1 Generator Work?
The SHA-1 generator’s process is both elegant and efficient. Here’s how it creates a unique hash from your data:
- Input Preparation: Submit your data—no matter the size or type.
- Padding: The input is padded to fit the algorithm’s 512-bit block structure.
- Processing: Through five rounds of logical operations—AND, OR, XOR—and constant additions, the data is transformed.
- Output: A 160-bit hash emerges, ready for use in verification or storage.
This streamlined approach ensures quick results, making SHA-1 a favorite for rapid hashing tasks.
Key Benefits of Using a SHA-1 Generator
Not sure if a SHA-1 generator is right for you? Check out these compelling advantages:
- Lightning-Fast Performance: SHA-1 hashes data in a flash, ideal for large files or real-time applications.
- Legacy Compatibility: Perfect for maintaining older systems or verifying vintage software.
- File Integrity Checks: Use it to confirm that files haven’t been altered during transfer.
- Free and Accessible: Online SHA-1 generators abound, and libraries are available in Python, Java, and more.
For non-security-focused tasks, SHA-1 remains a trusty companion.
How to Use a SHA-1 Generator: A Quick Tutorial
Getting started with a SHA-1 generator is a breeze. Follow these steps to create your hash:
- Choose Your Tool: Pick an online SHA-1 generator or install a library like hashlib in Python.
- Enter Your Data: Type your text or upload a file to hash.
- Generate the Hash: Hit “generate,” and your 40-character hash appears instantly.
- Apply the Result: Use it to verify data or integrate it into your project.
It’s simple, fast, and requires no technical wizardry!
SHA-1 Generator in 2025: Strengths and Caveats
Let’s set the record straight: SHA-1 isn’t bulletproof. Its vulnerability to collision attacks—where two different inputs yield the same hash—has relegated it from high-security roles since 2017. Modern alternatives like SHA-256 or Whirlpool outclass it for sensitive applications. That said, SHA-1 shines in 2025 for lightweight tasks like Git repository hashing, file deduplication, and legacy system support. It’s not about replacing it—it’s about using it wisely.
Turbocharge Your SEO with SHA-1 Generator Know-How
Want to climb Google’s ranks? Weave in keywords like “SHA-1 generator online,” “free SHA-1 hashing tool,” and “how to use SHA-1 generator.” Share this guide, link to a SHA-1 generator, and draw in tech enthusiasts and developers searching for hashing insights. Your site’s traffic will soar as you establish authority in this niche.
Final Thoughts: Why a SHA-1 Generator Still Holds Value
In 2025, a SHA-1 generator isn’t the ultimate security shield, but it’s far from irrelevant. Its speed, compatibility, and ease of use make it a standout for file verification, legacy maintenance, and educational purposes. Whether you’re a coder preserving old projects or a business ensuring data consistency, SHA-1 delivers where it counts.
Ready to give it a spin? Test a SHA-1 generator today and tap into its practical power. For critical security, look elsewhere—but for quick, reliable hashing, SHA-1 is a classic worth keeping in your arsenal!